Cybersecurity is a high-priority critical issue for businesses, and one that must be taken seriously. Cybersecurity threats include malware, spying, and data theft, and they can come from anywhere, including cyber criminals and nation-states. One of the most common ways that cybersecurity threats can enter a business is through the internet. Cybercriminals can use malware to steal data or hijack systems, and nation-states can use spyware and malware to monitor or steal data. To protect against these types of threats, businesses should have a carefully designed comprehensive cybersecurity plan. They should have an understanding of the types of threats that are out there, and they should have a plan for responding
Here we explain how Cybersecurity Culture can be addressed, Managed and implemented in any organization.
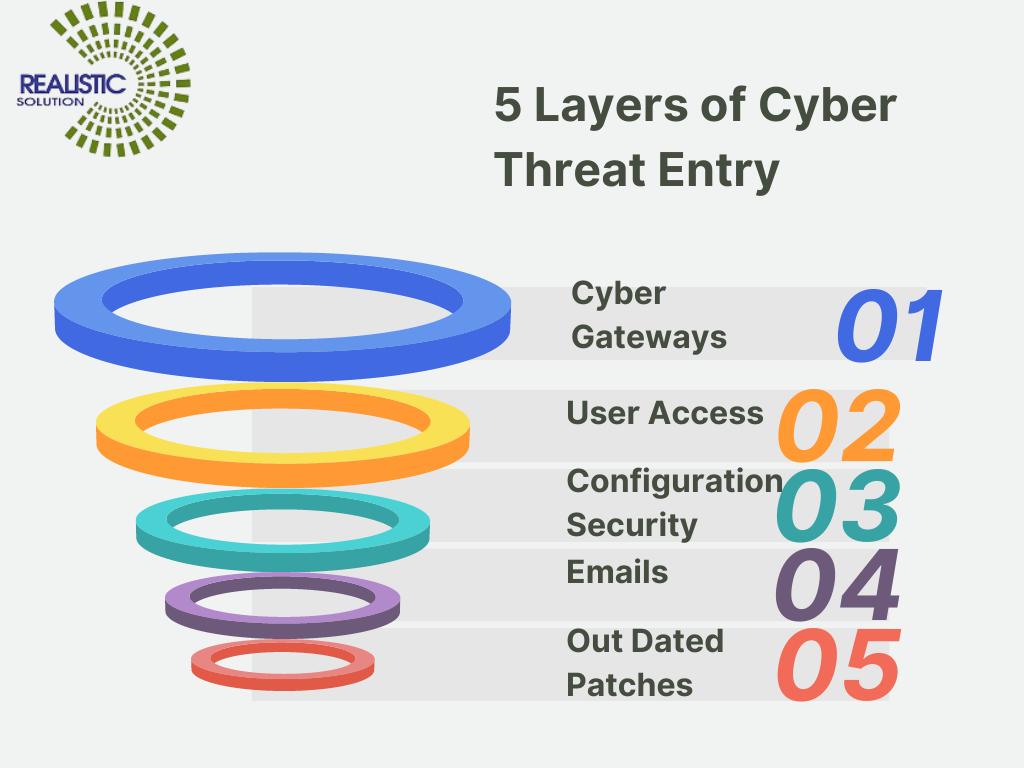
- Protect your Cyber Gateways:
Cyber-gateways include Firewalls, UTM , Bridge Mode Devices etc.
Configuring these entry points carefully , Professionally can assure safe Internet based activities in any organization.
- User Access:
Who can access What?
This is something to be decided very Carefully and it may require several sessions of brainstorming within the high level meetings of any organization.
This may include access of :
- Emails,
- Website access
- Server rooms , Servers access
- Gateways access
- DVR access
- DVR mobile access
- PABX access
- Configuration Security:
Configuration of all above-mentioned areas
- Emails:
To ensure Emails are delivered free of SPAM. Phishing, Dangerous attachments,
An organization may use many tools.
- Outdated Patches:
If Patches of Operating System and other installed base of programs is not up-to-date, this is a clear threat inviting Malware Ransomware, Exploits, and many complicated risks.
There must be a plan to stop the threat at the Entry Points.