BPO SERVICES
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nullam ac laoreet lacus. Morbi auctor quam tempus massa vestibulum aliquet eu lorem ipsum dolor sit amet consecteuter vitae ligula.
Information
About Our Services
AT Realistic Solution, you will find Quality of following services:
- Application Processing
- Product Renewals
- Records Management
- Transaction Processing
- Records Management

Who we are
About Us
Our company was founded in 2004.
We have achieved a confidence and trust of our customers in throughout globe.

Good choice
High quality and nice prices

Quality assurance
The quality is our pride

Easy to order
One-click order

Fast shipping
Only the best delivery services
ABOUT OUR PRODUCTS
Types Of Services
- Application Processing
- Product Renewals
- Records Management
- Transaction Processing
- Recoveries processing

Recent Posts
Our Blog

DNS Security Best Practices: A Quick Guide
DNS Security Best Practices: A Quick Guide On-premises traditional DNS Servers or ISP provided DNS Servers cannot analyze and prevent or filter resolution of domains server based on Command & Control except blacklisted ones in web filtering. The hackers use HTTP or HTTPS protocol for resolving the DNS for their spying .Or Alternately they can […]
- Post author By Engr. M Naeem Akhtar
- January 4, 2023
- No Comments on DNS Security Best Practices: A Quick Guide
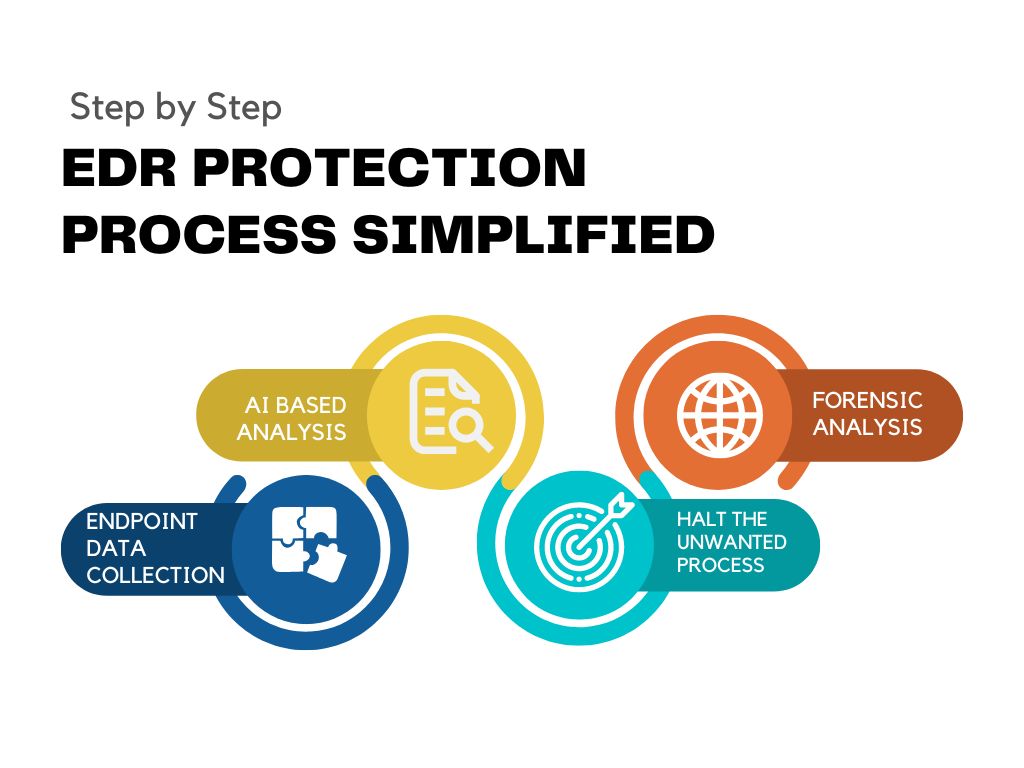
EDR Protection against Malware
EDR Endpoint Detection and Response against Malware is based on a unique Protection System. To Analyze EDR , you must have a basic idea, of what does the Malware/ Virus/ Threat does when it reaches the EndPoints: Possibilities are : 1-It May Initiate some processes unwantedly , and on an abnormally high scale. 2- It […]
- Post author By realisticadmin
- November 14, 2022
- No Comments on EDR Protection against Malware

What is Endpoint Detection and Response?
EDR Endpoint Detection and Response: It is a type of protection that offers Activity based Analysis of Malware , Halts the unwanted processes and offers Forensic Analysis. AI based EDR s can definitely stop Ransomware threats.
- Post author By realisticadmin
- November 14, 2022
- No Comments on What is Endpoint Detection and Response?












