
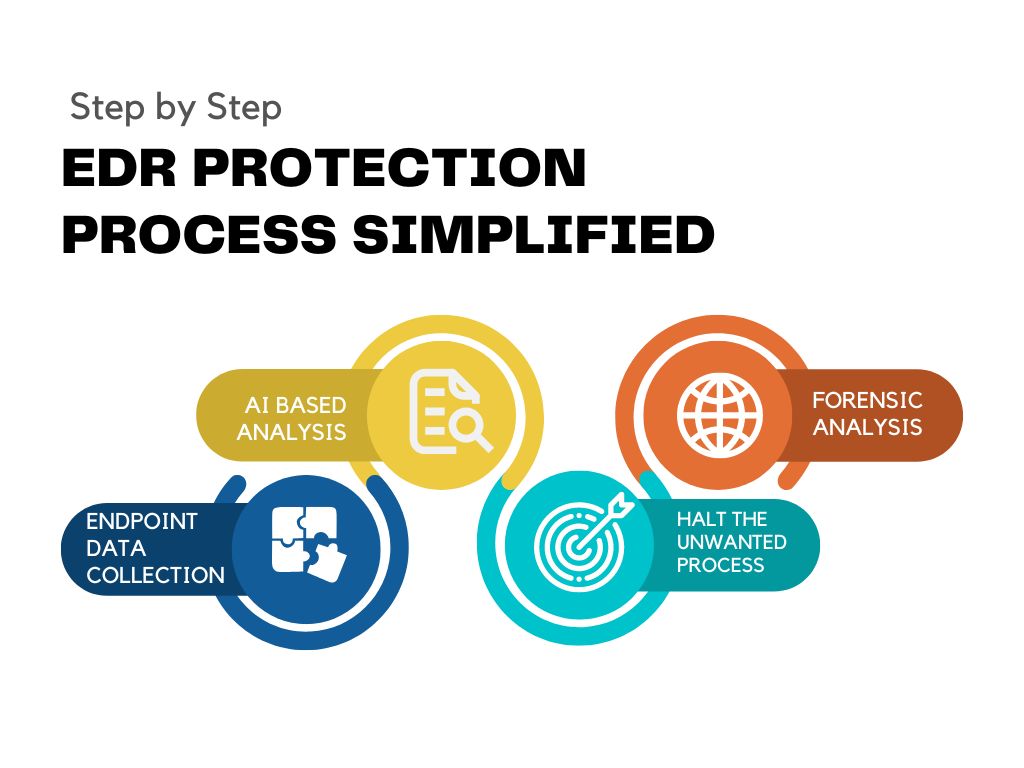
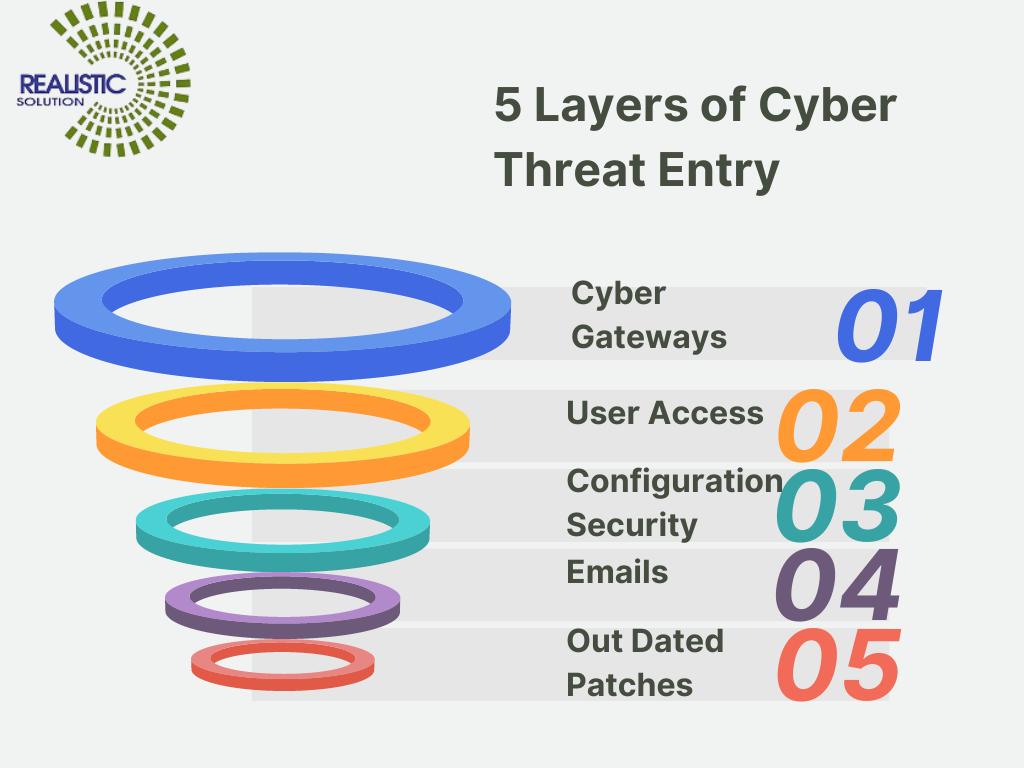
DNS Security Best Practices: A Quick Guide
DNS Security Best Practices: A Quick Guide On-premises traditional DNS Servers or ISP provided DNS Servers cannot analyze and prevent or filter resolution of domains server based on Command & Control except blacklisted ones in web filtering. The hackers use HTTP or HTTPS protocol for resolving the DNS for their spying .Or Alternately they can […]



Recent Comments