DNS Security Best Practices: A Quick Guide
On-premises traditional DNS Servers or ISP provided DNS Servers cannot analyze and prevent or filter resolution of domains server based on Command & Control except blacklisted ones in web filtering. The hackers use HTTP or HTTPS protocol for resolving the DNS for their spying .Or Alternately they can try encrypting servers access so that no one can identify where they have made a connection. So the DNS security is the first line of Defense in getting Ransomware protection. 95% of the ransomware attacks are just blocked if you have the Heimdal Machine Learning Security DNS Protection. This module is based on two proprietary technologies;
- DarklayerGuard TM
- VectorN Detection TM
It has cutting edge over its competitors like Cisco Umbrella or other DNS security solutions provided by Palo alto, Crowd strike, Sentinel One, Carbon Black, Kaspersky, TrendMicro, Sophos, Bitdefender, etc.
It’s critical to keep in mind that DNS requests and responses can provide a wealth of security-related data about user & network activity. Both authorized and potential cybercriminal users can learn a great deal about a company’s infrastructure from the DNS records alone.
To collect the user’s DNS Data criminals or hackers deploy rouge DNS servers and divert the legitimate website to a phishing website by diverting to a different IP. If the DNS query is not resolving back to the website domain then the DNS Security should block access to that website. Very simple trick but you should be using a smart and intelligent DNS Security solution.
Heimdal machine-learning based DNS Security solution is the next-generation security solution to secure from malicious DNS queries. When designing a safe and dependable Secure DNS infrastructure, we take into account the following DNS Security Best practices.
Conceal your primary servers
Your DNS security should be intelligent enough to find the Primary DNS for the domain your system is attached to. When you provide the Primary DNS server in the DNS Configuration the viruses or the criminals immediately come to know where to attack so that your accounts get locked and you are unable to use your infrastructure. The Heimdal Machine Learning DNS security uses loopback IP as a Primary DNS server for each machine, all DNS packets over UDP or TCP or HTTP, or HTTPS protocols are readable and these are filterable. When we use local loop-back as a DNS server no one can find the DNS records of the other machines or servers. (see snapshot below)
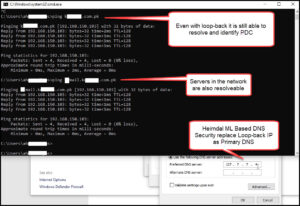
using local loop-back as a DNS server
USE DNSSEC to safeguard the integrity of your data
Domain Name System Security Extensions (DNSSEC) should be used whenever possible, especially with zone data that is accessible to the general public. To guarantee the accuracy of the data being delivered. DNSSEC digitally signs DNS information so nameservers may validate its accuracy before responding to queries with it. The Internet Corporation for Assigned Names and Numbers (ICANN) asserts that full DNSSEC deployment will assist in ensuring that end-users are connecting to the genuine website or any other service associated with a specific domain name. Public key infrastructure (PKI) is used for this authentication, creating a chain of confidence between the root server located at the top of the DNS tree and the lowest end nodes, or the nameserver for the end user.
Does an Antivirus solution not enough?
Antivirus solutions are no longer enough to keep an organization’s DNS systems secure. HEIMDAL® ML Based DNS Security Module is next generation proactive shield that stops unknown threats before they reach your system. Machine learning-powered scans for all outgoing DNS traffic. Stops data breaches before sensitive info can be exposed to the outside. Advanced DNS, HTTP, and HTTPS filtering protect your endpoints against data leakage, APTs, ransomware, and exploits.
Try it for FREE today
30-day Free Trial. Offer valid only for companies.
How Realistic Solution can help you?
We will design the security posture for your company including DNS filtering as the first stage toward a secure DNS. Even if it isn’t exactly a novelty in cybersecurity or a match to DNSSEC, it is nonetheless important. A strong DNS filtering engine like the one used by Heimdal® Threat Prevention is more than capable of catching malicious data packets that could damage your endpoints and network. Our design reduces latency by using both local and cloud queries. The DNS traffic filtering engine examines packets each time your machine performs a DNS query to check for anything suspicious hidden in the Internet traffic. Remember adopting DNS Security Best Practices: A Quick Guide for Organizations can really make a difference, and your organization can feel secure in the robust IT era.


One reply on “DNS Security Best Practices: A Quick Guide”
Excellent knowledge sharing.